4 min read
The Evolution of Authentication
From Passwords to Passkeys
The History of Passwords
Passwords have been the cornerstone of digital security since the inception of the internet. They serve as the first line of defense, protecting our personal information, financial data, and digital identities. However, as cyber threats have evolved, the vulnerabilities of traditional passwords have become increasingly apparent.
Hackers have developed sophisticated methods to crack passwords, from brute force attacks to phishing scams. Moreover, the human factor often proves to be the weakest link in password security. The challenge of remembering multiple complex passwords often leads to the use of weak or repeated passwords, further compromising security.
The Advent of Passkeys
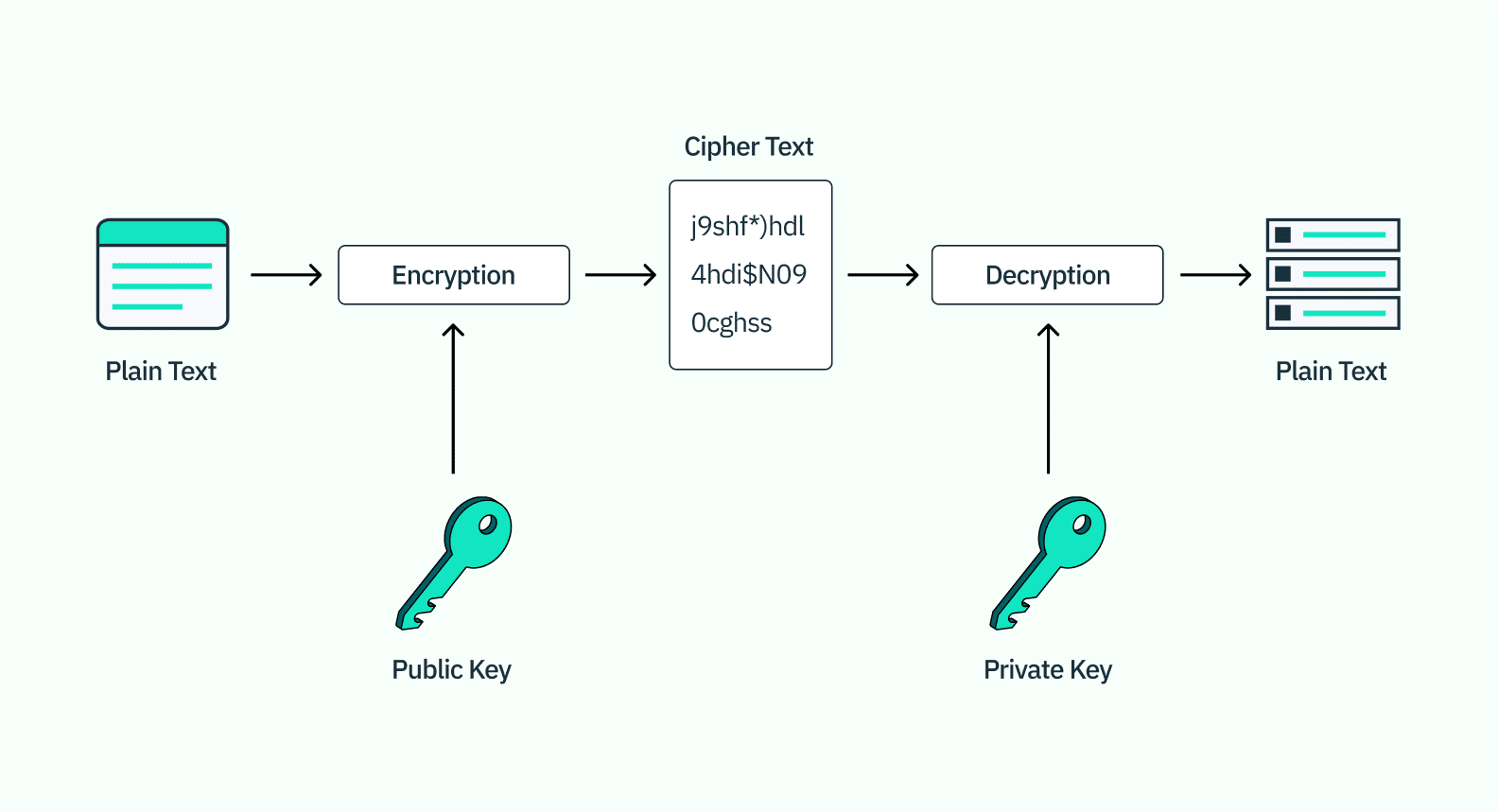
In response to these challenges, the tech industry has been exploring alternatives to passwords. One such alternative is the use of passkeys. A passkey is a cryptographic entity that’s not visible to the user and is used in place of a password. It consists of a key pair: one key is public, registered with the website or app you’re using, and the other key is private, held only by your devices.
Google, Apple, and Microsoft are at the forefront of this shift. They are implementing passkeys as a more secure and user-friendly method of authentication. The goal is to replace passwords with passkeys, allowing users to authenticate using biometrics such as fingerprints or face scans, or a device PIN.
The Journey Towards Universal Adoption
The universal adoption of passkeys, however, depends on several factors. Firstly, individual websites and apps need to implement this technology, which could require significant changes to their existing authentication systems. Secondly, users need to understand the benefits of passkeys and feel comfortable using them. Lastly, for a truly universal experience, passkeys need to be supported across all devices and operating systems.
How to Use Passkeys
Using passkeys is designed to be straightforward and intuitive. On Google, you can create a passkey for your Google Account by visiting g.co/passkeys and following the instructions to add the security key that’s built into your phone or a standalone security key.
For Apple users, the latest iOS 17 and macOS Sonoma betas have introduced support for passkeys for Apple IDs. This allows users to sign in anywhere that supports signing in with an Apple ID — including Apple.com, icloud.com, and any other linked sites — without passwords, using just the biometrics on their iPhone or MacBook.
Microsoft, on the other hand, supports passkeys as a common passwordless sign-in method. Microsoft’s passwordless authentication, which includes Windows Hello, security keys, and Microsoft Authenticator, can help organizations eliminate password vulnerabilities while providing fast, safe access across the enterprise.
The Security of Passkeys
One of the key advantages of passkeys is their inherent security. But what happens if a key becomes compromised?
If the public key associated with a passkey becomes compromised on the website or app you’re using, it would not directly lead to a security breach. This is because the public key is designed to be shared and is useless without the corresponding private key, which is securely stored on your device and never shared.
However, if the private key becomes compromised, that would be a serious security issue. The attacker could potentially impersonate the user and gain unauthorized access to their accounts. To mitigate this risk, private keys are typically stored in a secure area of the user’s device, such as a secure enclave in modern smartphones or hardware security modules in servers. These areas are designed to resist tampering and extraction of the keys.
Furthermore, if a key is suspected to be compromised, it can be revoked, and a new key pair can be generated. The revocation would be communicated to the website or app, which would then refuse to authenticate using the compromised key.
In addition, the use of biometric data (like fingerprints or face scans) or device PINs adds an extra layer of security. Even if someone were to gain access to your device, they would still need your biometric data or PIN to use the passkey.
In conclusion, while no security measure is completely foolproof, the design of passkeys and the security measures in place make them a significantly more secure alternative to traditional passwords. The shift from passwords to passkeys is not just about convenience, but also about enhancing the security of our digital lives.
The Future is Passwordless
The shift from passwords to passkeys marks a significant evolution in digital security. As Google, Apple, and Microsoft continue to innovate and push for the adoption of passkeys, we are moving closer to a future where the best password is no password at all. However, the journey towards this passwordless future will require widespread implementation, user adoption, and cross-platform compatibility. As we navigate this transition, the promise of a more secure and user-friendly digital experience awaits us.

